General Study of Digital Signature Schemes
AzamjonAbdullaeva, Mohammed AbdulhakimAl-Absia, AhmedAbdulhakim Al-Absib,
MangalSainc, Hoon Jae Leec
aDepartment of Ubiquitous IT, Graduate School, Dongseo University, 47 Jurye-ro, Sasang-gu, Busan 47011,Republic of Korea
bDepartment of Smart Computing, Kyungdong University 46 4-gil, Bongpo, Gosung, Gangwon-do,
24764, Republic of Korea
c Division of Information and Communication Engineering, Dongseo University, 47 Jurye-ro, Sasang-gu, Busan 47011, Republic of Korea
Azamjon.a.sobirovich@gmail.com, Mohammed.a.absi@gmail.com, absiahmed@kduniv.ac.kr, mangalsain1@gmail.com, hjlee@dongseo.ac.kr
Abstract
Digital signatures are fundamental in today’s modern world to verify the sender of a document’s identity. Digital signature is performing in the computer as a string of binary. Signature is computer utilizes a set of principles and parameters such that identification and authenticity of the data can be confirm. The main objective of this work is to have general information about digital signature schemes.
Keywords: Digital Signature schemes, DSA, ECDSA, RSA
1. Introduction
The signature is created by the use of a private key. Only to the user is known the private key. The signature is verified makes use of a public key which match to the private key. Every user has onepublic key and one private key pair. Public keys are known by everyone, and can be used to verify the user signature. However private key is not shared, private key is used in generation signature, which is done only by the user [1].
Digital signatures used to reveal unauthorized amendment to data. However, the recipient of a digitally signed document in proves to a third party that the document was indeed signed by the human who it is assumed to be signed. This is recognized as nonrepudiation, because the human who signed the document cannot refuse the signature at a later time. We can use Digital signaturealgorithm in electronic funds transfer, e-mails, data storage, electronic data interchange, software distribution, and just about any application that would need to assure the integrity and originality of data [2].
The Digital Signature Algorithm (DSA):
DSA is specified in DSS. The specification includes criteria for the generation of domain parameters, for the generation of public and private key pairs, and for the generation and verification of digital signatures.
The RSA Digital Signature Algorithm:
RSADSA is specified in American National Standard (ANS) X9.31 and Public Key Cryptography Standard (PKCS) #1. FIPS 186-4 approves the use of implementations of either or both of these standards and specifies additional requirements.
The Elliptic Curve Digital Signature Algorithm (ECDSA):
ECDSA is specified in ANS X9.62. FIPS 186-4 approves the use of ECDSA and specifies additional requirements. Recommended elliptic curves for Federal Government use are provided herein.
The public key is used in the signature verification process. The public key need not be kept secret, but its integrity must be maintained. Anyone can verify a correctly signed message using the public key [3].
For both the signature generation and verification processes, the message (i.e., the signed data) is converted to a fixed-length representation of the message by means of an approved hash function. Both the original message and the digital signature are made available to a verifier (Fig. 1).
 |
Fig. 1 Digital Signature Processes [5]
2. Applications of digital signatures
Digital signatures can supply assertion of the evidence to exporter, identity, and status of an electronic document and acknowledging informed approval of the site by a signatory [4].
Integrity: There are status where is a need for dependability where the message has not been changed during transmission. However, if a message is digitally signed, any modification in the message after signature will abrogate the Digital signatur.
Authentication: to authenticate the origin of message, we can use digital signatures. For instance, Alice will sends Bob the encrypted message digest. In order for Bob to authenticate the signature he should apply the same hash function as Alice to the message she sent to him. He will also decrypt the encrypted message using Alice is public key and compares the two. If the two are the same then he has successfully authenticated the signature. If the two are not match then either an error happen through transmission or someone was trying to impersonate Alice. However, valid signature display that the message was sent by the ownership user, when the digital signature of the ownership is constrained to a particular user.
Non-repudiation: here the information that we may have received can be definitely attributed to somebody and there is no way that they can take it back. They definitely said what is that we have in this message right here.
3. Different types of digital signatures
· Digital Signatures with appendix: Require the message as input to the verification
· Digital signatures with message recovery: A priori knowledge of the message is not required for the verification algorithm
· Digital signatures based on RSA:Includes the features of both Digital Signatures with appendix and Digital signatures with message recovery
· Blind signature schemes: Allows sender A to remain anonymous so that spending patterns cannot be monitored
4. Comparison of Security Levels
An elliptic curve, defined modulo a prime p, is the set of solutions (x, y) to an equation of the form:
y2 = x3 + ax + b (mod p)
For two numbers a and b.
If (x,y) satisfies the above equation
then P=(x,y) is a point on the elliptic curve.
In fact, an elliptic curve can also be defined over the finite field consisting of 2m elements. Such a representation offers extra efficiency in the operation of the ECC.
Using some particularly deep mathematics, it is possible to define the “addition” of two points on the elliptic curve.
Suppose P and Q are both points on the curve, then P + Qwill always are deferent point on the curve. The elliptic curve discrete logarithm problem can be stated as follows. Fix a prime p and an elliptic curve. xP represents the point P added to itself x times. Suppose Q is a multiple of P, so that Q = xPfor some x. Then the elliptic curve discrete logarithm problem is to determine x given P and Q.
Fig. 2 compares the time required to break the ECC with the time required to break RSA or DSA for various modulus sizes using the best general algorithm known. The values are computed in MIPS years. A MIPS year represents a computing time of one year on a machine capable of performing one million instructions per second. As a benchmark, it is generally accepted that 1012 MIPS years represents reasonable security at this time, since this would require most of the computing power on the planet to work for a considerable amount of time.
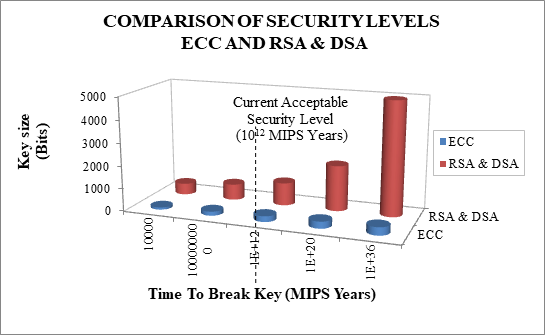
Fig. 2 Comparison of Security Levels
Therefore, from the figure, we see that to achieve reasonable security, RSA and DSA should employ a 1024-bit modulus, while a 160-bit modulus should be sufficient for the ECC. Not only can it been seen that the ECC requires a much smaller modulus than RSA or DSA, but also that the security gap between the systems grows as the key size increases. For example, 300-bit ECC is a great deal more secure than 2000 bit RSA or DSA.
4. Conclusion
Digital signatures are fundamental in today’s modern world to verify the sender of a document’s identity. In this paper we perused the concept of general informationabout Digital Signature Processesdigital signaturesapplications, different types of digital signature with the Comparison of Security Levels. Electronic digital signature (EDS) has eliminated most of the problems inherent in the signature on a paper document; however the future work would consider theproof of identity of who sent the document and confirmation of the authenticity of the document.
Acknowledgment
This work was supported by Institute for Information and Communications Technology Promotion(IITP) grant funded by the Korea government(MSIT) (No.2018-0-00285)
References
[1] Boyd C. (1986). Digital multi-signature, In Cryptography and Coding. Editors, Beker H.J. and Piper F. C., Clarendon Press, London, p.p. 241 –246.
[2] D. Stinson, Cryptography, Theory and Practice, CRC Press, Second edition, 2000.
[3] W. Stallings, Cryptography and Network Security: Principles and Practice, Second edition, Prentice Hall, 1999.
[4] J. Menezes and P. C. van Oorschot and S. A. Vanstone, Handbook of Applied cryptography, vCRC Press, 1996.
[5] Joselin.j, s.J.Brintha, V.Magesh Babu”Role of Digital Signature in Network Security and Cryptography” (IJCSIT) International Journal of Computer Science and Information Technologies, Vol. 6 (1), 2015, 893-895